Like most people you probably feel reasonably safe on your PC. After all Microsoft/Apple is sending updates all the time it seems.
But what about all the other software you rely on. What about the software you installed years ago and haven't used since.
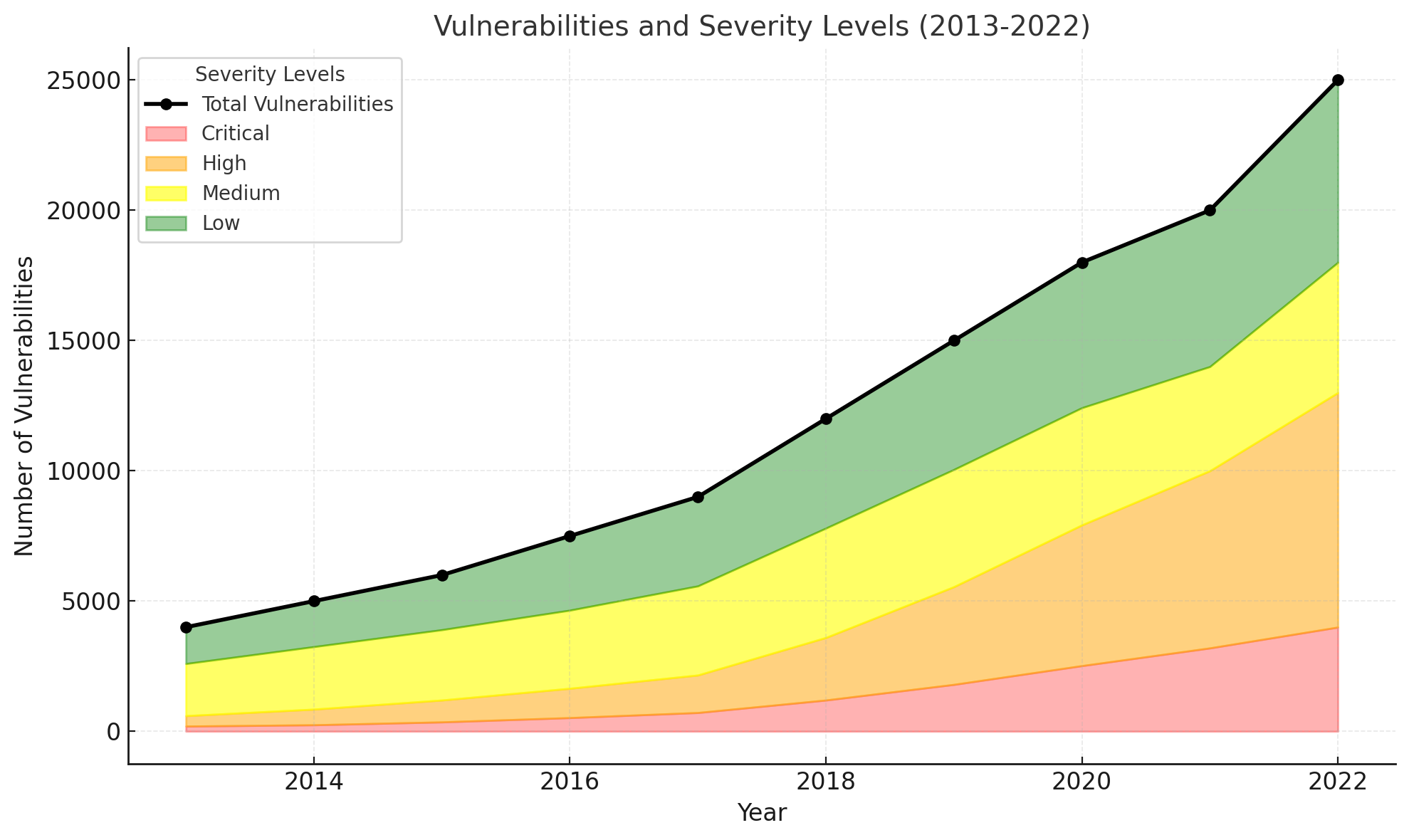
The average number and severity of vulnerabilities discovered over the last 10 years is increasing alarmingly:
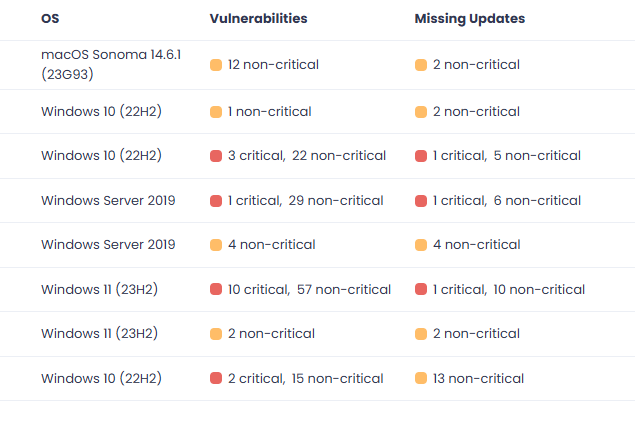
Most people are surprised when I scan their PC for vulnerabilities and find results like this:
(Don't worry, these computers are in my Test environment and perfectly safe!)
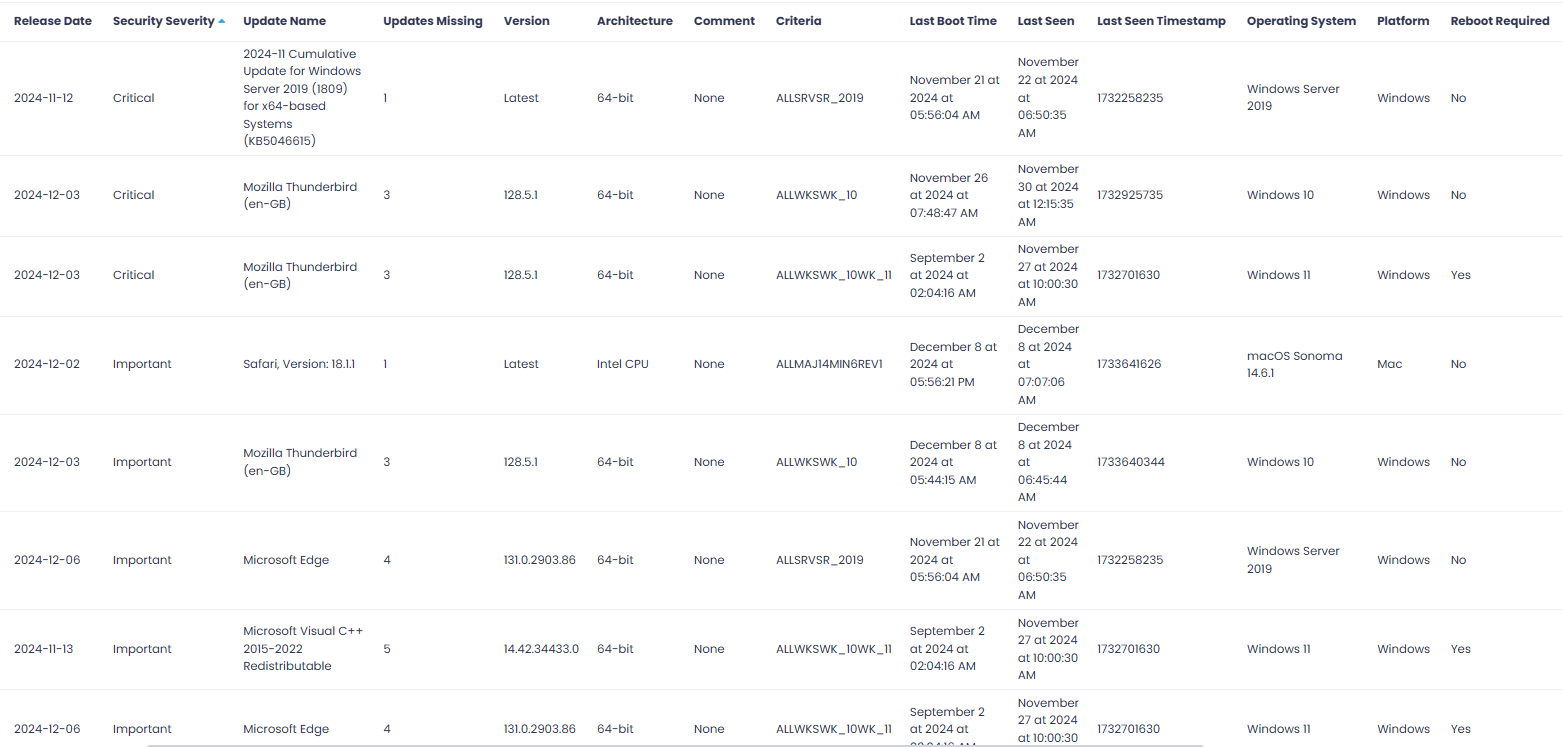
Here is a list of the missing updates sorted by severity:
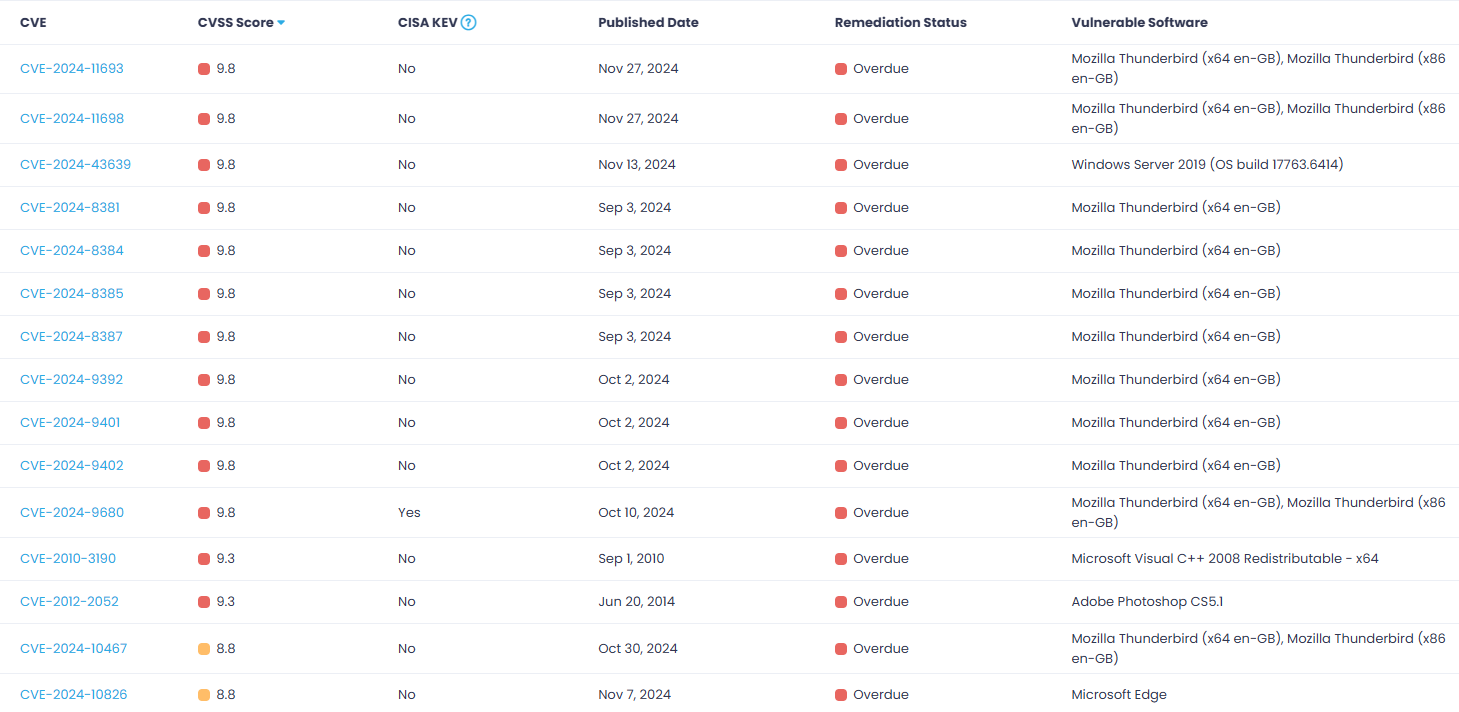
The worrying part starts when you look at the individual vulnerabilities that remain unpatched due to the missing updates:
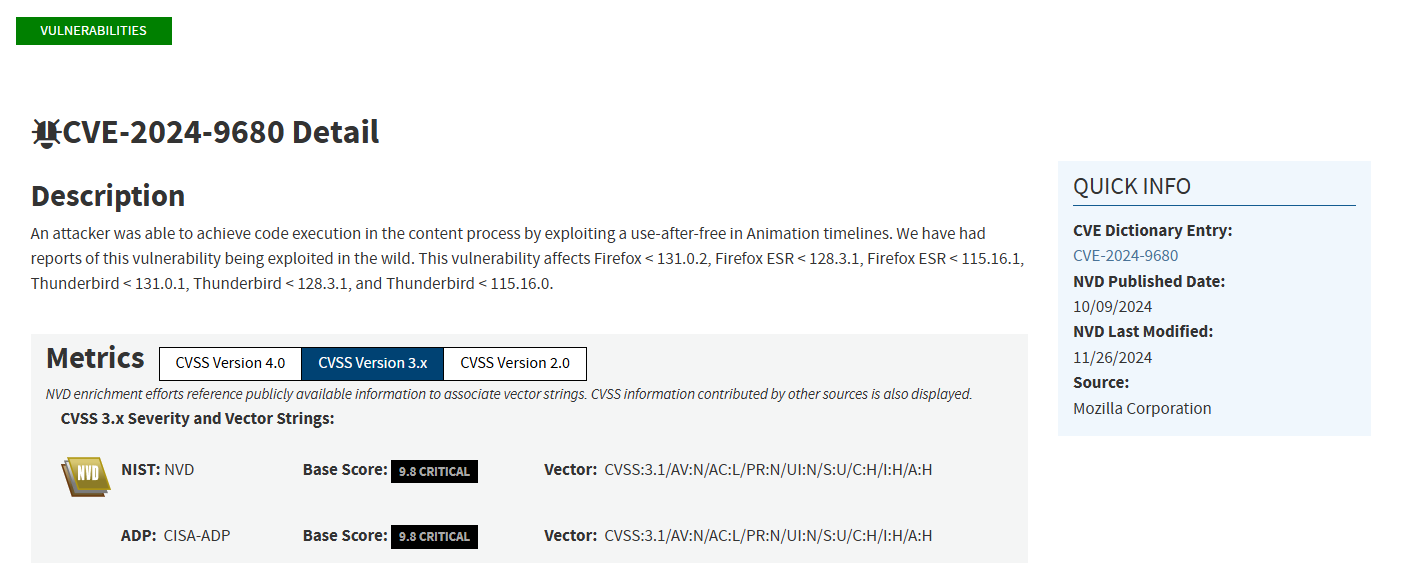
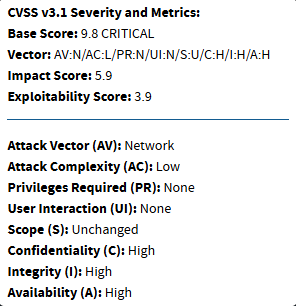
Looking further at the 11th vulnerability in the list:
The first thing to note is the CVSS score of 9.8. Yes that's out of 10 and higher is more dangerous. Second thing is that the vulnerability is listed on the CISA KEV list which means that this vulnerability has been seen being actively exploited by malicious actors.
The reasons for that high score are broken down in the chart:
Attack Vector - Network means that the bad actor can exploit this vulnerability without having direct access to your PC.
Complexity - Low means that the exploitation is fairly easy to accomplish.
Privileges Required - None means that the actor does not need your login password to accomplish the exploitation of your PC.
User Interaction - None means that they do not require you to assist by tricking you to click on something. In fact they can do this without you noticing.
As you can see the situation with these mostly up to date PCs in my Testlab is potentially problematic if they were exposed to the Internet.
Fortunately the resolution to all of these vulnerabilities is quick and easy.
The hard part is being aware that the vulnerabilities exist and to realise the danger they represent.
Dont be this guy:

Hope Computing wants to help.
The Hope Computing Vulnerability Management service starts with a small piece of software called an agent being installed on your Windows or MacOS computer.
Whenever your computer is online, the agent will forward information about the software installed on your PC and the versions installed. This includes the software, drivers (software that makes the hardware components and peripherals like printers monitors keyboard etc work), even the BIOS version (this is the very first software that starts when you power up your PC and has access to the base components of your PC).
Hope Computing will assess the information provided and workout a plan to install patches or apply workarounds to ensure you are as safe as possible.
The cost is small compared to the loss of control of or access to your data.
Hope Computing's Vulnerability Management service consists of:
- Initial scan upon agent installation
- Initial vulnerability report with discussion of findings
- Regular scanning when online
- Monthly patching schedule
- Urgent updates as required
Vulnerability Management forms a part of an overall Cybersecurity defence plan by removing avenues for attacking your systems.